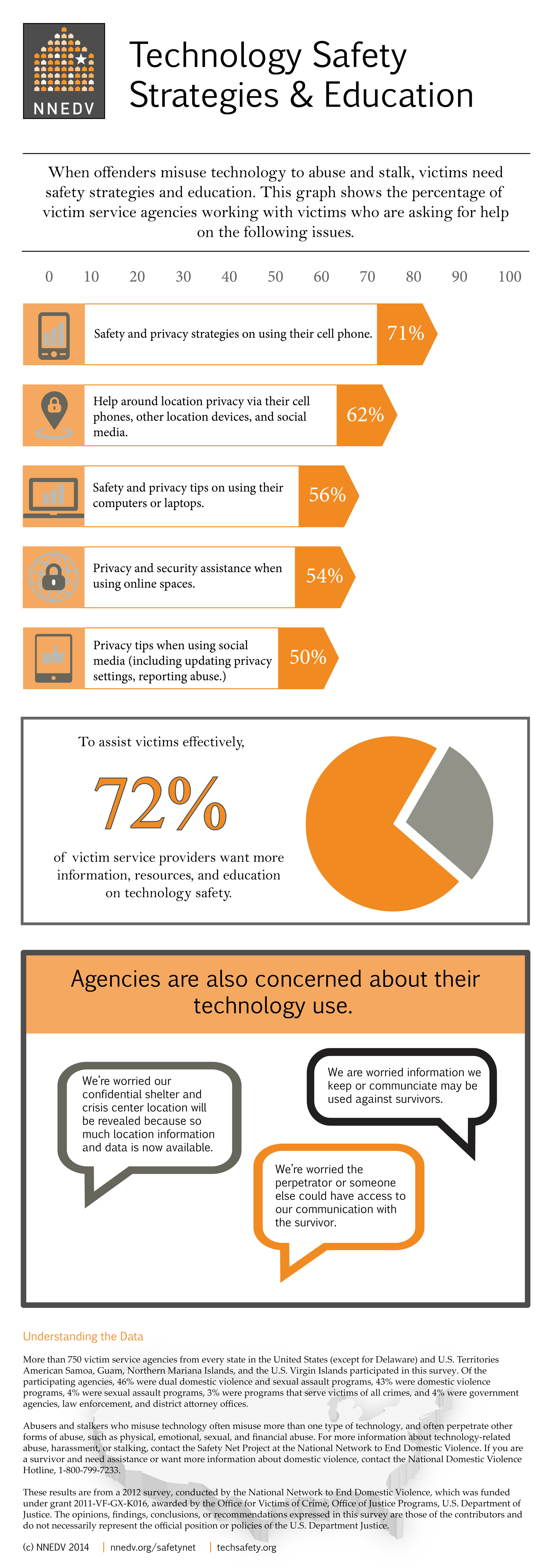
Cell Phone Location, Privacy and Intimate Partner Violence
/The Domestic Violence Report recently published an article Safety Net wrote on cell phone location privacy and safety. This comprehensive article discusses how cell phone location is misused by abusers to stalk and monitor victims and tips on what victims can do. It explores the different ways cell phone location information can be revealed and concludes with proposed federal legislation on location privacy and best practices for app developers who want to collect location information through their apps. Read the full article.
photo: Ron Wiecki
Meanwhile, here are a few safety tips on what to do if someone is misusing your cell phone location information as a tool to monitor or stalk you.
1. Safety first. If removing the tracking app or turning the phone off may be more dangerous, develop a safety plan regarding how to continue using the phone so that the abuser does not become suspicious. Simultaneously create a plan on how to communicate with others until the program can be removed completely or you’re able to get a new phone.
2. Keep a log. Knowing the pattern of the abusive person’s behavior and what information they seem to know can help the survivor narrow down how the abuser is getting his or her information. Abusers can be creative and can find many ways to monitor and stalk a victim, often using more than one technology or method.
3. Secure your phone. Become familiar with the security settings and put a lock code on the phone.
4. Don’t install unknown apps or programs. Be careful not to install programs that are unknown, especially if the suggested app is from the abuser or mutual friends. Also, be aware of what permissions or access to data on your phone that the app requires before you download.
5. Limit apps that are using your location. Know which applications are using your location and either limit its ability to use your location or delete the app, unless you are confident in what the purpose is and the extent of the sharing and access to your personal information.
6. Use privacy settings. If a location program is already on the phone, the user should learn about its settings and features. Knowing what controls are available may allow for continued use while also maintaining privacy and control.
7. Turn off phone. For short periods of time, a survivor can cut off communication from the phone by putting the phone on airplane mode or turning the phone off and taking out the battery. However, be aware that when the phone is turned back on, all communications will continue and location information may be shared again.
8. Start fresh. When getting a new cell phone, don’t import everything from the old phone to the new one. Porting over all the data may inadvertently install the tracking application as well.
Want a more thorough safety plan? Download our Cell Phone & Location Safety Strategies handout.